
Victoria - Fotolia
Comparing SASE vs. traditional network security architectures
Today's dispersed environments need stronger networking and security architectures. Enter cloud-based Secure Access Service Edge -- a new model for secure network access.
Late 2019 brought the emergence of a new cloud-based architecture service model dubbed Secure Access Service Edge, or SASE, by Gartner. SASE represents the convergence of networking service brokering, identity service brokering and Security as a Service into a single unified fabric.
Here, uncover which organizations may want to consider SASE adoption, how the model differs from traditional network security and considerations for choosing a SASE provider.
Where SASE fits in
The biggest advantage of SASE is the convergence and unification of numerous disparate network services into a single brokering fabric for both edge environments and stand-alone users. This helps improve security by reducing the complexity and lack of interoperability of traditional approaches that often require numerous vendors and services to achieve the same control implementation. However, note that not all services offered by SASE providers are mature or comparable in features to more established standalone products and services sold by traditional vendors.
There are several SASE use cases that may be appealing or interesting to organizations rapidly shifting to use more cloud services. These include the following:
- Core network. For internal users and services that need to access cloud services, SASE may replace cloud access security brokers (CASBs) and other brokering options to access cloud securely.
- IoT and edge computing. IoT and edge network scenarios can be isolated and connected through network-restricted policies assigned within a SASE brokering service or in tandem with software-defined WAN (SD-WAN) vendors.
- Branch. Branch locations can connect to on-premises and cloud resources through SD-WAN and SASE brokering instead of traditional network service providers.
- Remote end users. Remote end users can connect to SASE services to receive access policies traditionally applied by internal VPNs. SASE essentially offers a VPN as a service that can broker connections to any approved destination over a secure channel.
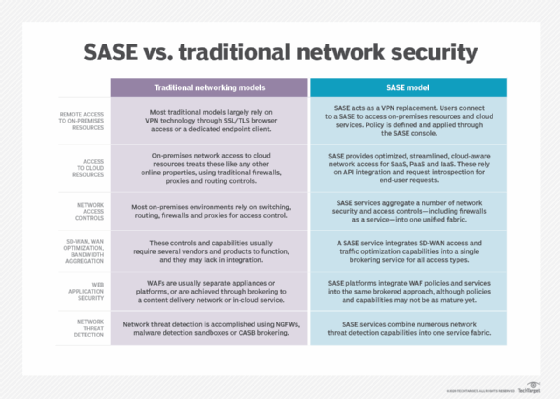
Comparing traditional networking models with SASE
As with any new service architecture, there is some confusion around the key differences between SASE vs. traditional network security, architectures and controls. The following table should help enterprise networking and security teams to gain a better understanding of these different areas.
Choosing a SASE provider
Gartner predicted 40% of enterprises will have SASE adoption plans by 2024. For organizations considering SASE providers based on networking and network security capabilities, take several key things into account. First, heavily scrutinize uptime and availability service-level agreements, along with the breadth in points of presence for connectivity. Second, carefully assess network and network security capabilities. Few SASE platforms are good at all network functions and services collectively, so evaluate their strengths and weaknesses. For example, some may excel at SD-WAN and traffic optimization, while others are more focused on CASB or VPN replacement.







