6 SaaS security best practices to protect applications
Use these SaaS security best practices to ensure your users' and organization's SaaS use stays as protected as the rest of your enterprise applications.
It is tempting to think that securing SaaS is fundamentally about users accessing the web. But, upon closer inspection, keeping SaaS use secure is much more complicated than it seems.
The truth is that there's no one-and-done, one-size-fits-all SaaS security checklist. Organizations vary; they do different things, operate differently and have different requirements.
That said, there are a few guidelines to follow when it comes to SaaS security. An organization's response should be predicated on its own usage, but following these six SaaS security best practices are near universal to properly defending SaaS applications.
Best practice #1: Enhanced authentication
Examining how users access SaaS resources in the first place is a wise starting point. But, because cloud providers may handle authentication in different ways, it can be a complicated process. Some providers offer the option of integrating with identity providers the customers manage, for example, with Active Directory (AD) via Security Assertion Markup Language, Open Authorization or OpenID Connect, while others do not. Some providers might give customers the option to enable multifactor authentication, while still others do not offer this capability.
This article is part of
What is cloud security management? Guide and best practices
To navigate this, it's important for security teams to understand what services are in use and what options are supported by each. With this context, admins can better select the authentication method(s) based on needs. If SaaS providers support it, single sign-on tied to AD can be a smart choice. This method ensures password and account policies correlate to what is in use for SaaS applications.
Best practice #2: Data encryption
Most channels used for communication with SaaS applications today employ TLS to protect data in transit. However, many SaaS providers offer an encryption capability to protect data at rest, too. For some providers, this is a default feature; for others, it must be explicitly enabled by the customer. To determine which applies to the services in use, teams need to research the security measures available. If given the option, enabling data encryption features is a good idea.
Best practice #3: Vetting and oversight
Just as organizations review and validate potential vendors, ensure this is done with SaaS providers as well. Understand the usage, the security model they employ to deliver their service and the optional security features available.
Best practice #4: Discovery and inventory
Looking for new SaaS usage that may not currently be tracked should be on every SaaS security checklist. One of the most compelling aspects of the SaaS model is the ability to rapidly deploy applications. As such, be alert for unexpected usage. When and where possible, employ both manual data gathering methods and automated tools to keep abreast of usage, and maintain a reliable inventory of what services are employed -- and by whom -- throughout the organization.
Best practice #5: Consider CASBs
In situations where a SaaS provider cannot provide the desired level of security, explore cloud access security broker (CASB) tool options. With a CASB, organizations can layer on additional controls not provided by the SaaS provider natively. These tools can be a great way to address limitations in the cloud provider's security model.
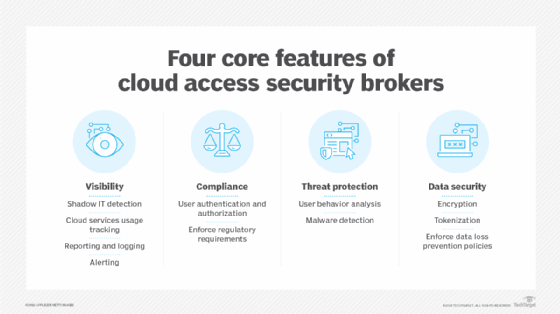
To get the most out of this SaaS security best practice, pay attention to CASB deployment modes. Make sure to select the right CASB deployment configuration -- be it proxy or API-based -- that makes the most sense architecturally for the organization.
Best practice #6: Maintain situational awareness
As always, monitor SaaS use. Examine data from internal tools, such as CASBs, as well as any logs or other information provided by the service providers.
It is important IT and security leaders understand that SaaS offerings are not "just another website." They are powerful tools that require the same degree of security as any other enterprise application. By adopting these SaaS security best practices in tandem with systematic risk management measures, organizations can ensure SaaS is employed safely by users and that SaaS usage stays protected.








