Use Azure Security Center to conduct a security posture assessment
In this excerpt from Chapter 4 of Microsoft Azure Security Center, the authors outline how to use the software to determine and improve your enterprise's cloud security posture.
Information security assessments are a critical component of any enterprise infosec program, helping organizations understand potential vulnerabilities in their systems and policies. As more modern workloads move to the cloud and expand the enterprise attack surface, the need for regular information security assessments is greater than ever.
An effective information security assessment will not only help enterprises identify the current state of their network, assets and users on premises and in the cloud, but also provide recommendations for how to improve weak controls and processes. Recent examples, like the WannaCry and Petya ransomware outbreaks, highlighted insecure configurations of many enterprise systems. Had teams conducted an information security assessment to determine which patches to apply and where holes needed plugging, the effects of the ransomware attacks could have been lessened.
There are many tools available to help enterprises conduct information security assessments, including Azure Security Center, Microsoft's security management system. In this excerpt from Chapter 4 of Microsoft Azure Security Center, Second Edition, published by Pearson Education, authors Yuri Diogenes and Tom Shinder outline how Security Center can be used to perform a security assessment on premises, in the cloud -- Azure or other providers -- and hybrid environments.
Read on to learn how to calculate your enterprise's current Secure Score -- Microsoft's measurement of the current security configuration of an organization's systems. Then, explore how to fine-tune your company's score to boost the safety and resiliency of your enterprise's assets.

Microsoft Azure Security Center, Second Edition
Click here to learn more about Microsoft Azure Security Center, Second Edition.
Download a PDF of Chapter 4.
Learn more about publisher Pearson Education.
Secure Score
When working in a cloud environment, monitoring the security state of multiple workloads can be challenging. How do you know if your security posture across all workloads is at the highest-possible level? Are there any security recommendations that you are not meeting? These are hard questions to answer when you don't have the right visibility and tools to manage the security aspects of your cloud infrastructure.
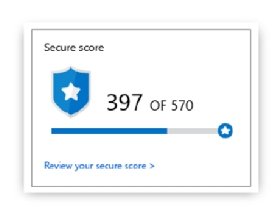
Security Center reviews your security recommendations across all workloads, applies advanced algorithms to determine how critical each recommendation is, and calculates your Secure Score based on them. Secure Score helps you to assess your workload security posture from a single dashboard. You can view the overall Secure Score in the Overview page in Security Center dashboard, as shown in Figure 4-1.
The overall Secure Score shown in the main dashboard is an accumulation of all your recommendation scores. Keep in mind that this score can vary because it reflects the subscription that is currently selected and the resources that belong to that subscription. If you have multiple subscriptions selected, the calculation will be for all subscriptions. The active recommendations on the selected subscription also make this score change. For the example, as shown previously in Figure 4-1, the current Secure Score of this subscription is 397 out of 570. This means that to achieve 570, it is necessary to address all current recommendations. To access more details about your Secure Score, click the Review Your Secure Score option in the Secure Score tile (see Figure 4-2).
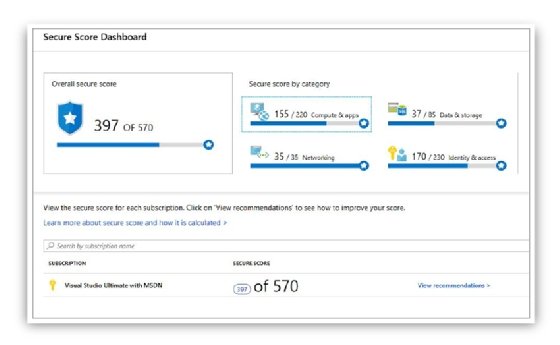
From this dashboard, you have a better visualization of how your workloads impact your overall Secure Score. The example shown in Figure 4-2 has an interesting breakdown because the Networking workload is fully compliant, but the other workloads are still a long way from being fully compliant. From here on, you can either click on each workload to see the recommendations or click view recommendations on the subscription. For this example, click the View Recommendations option to see all recommendations, as shown in Figure 4-3.
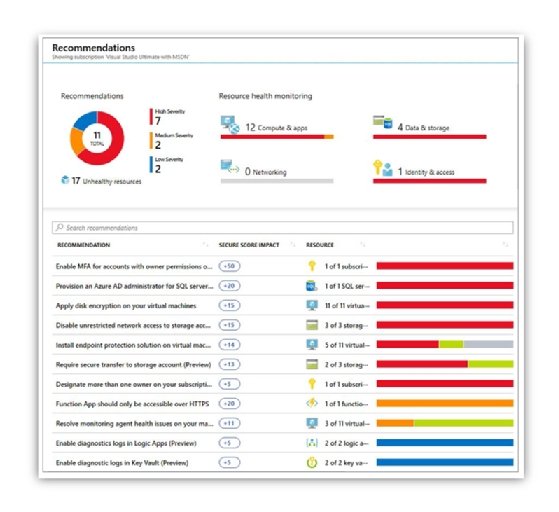
The recommendation Secure Score is a calculation based on the ratio between your healthy resources and your total resources. If the number of healthy resources is equal to the total number of resources, you get the maximum Secure Score of 50. To try to get your Secure Score closer to the max score, fix the unhealthy resources by following the recommendations. Notice that each recommendation has its Secure Score Impact; this number allows you to see how much your Secure Score will be impacted once you address this recommendation. For example, if your Secure Score is 50 and the recommendation impact is +5, performing the steps outlined in the recommendation will improve your score to 55.
Fine-tuning your Secure Score
While Secure Score can be utilized to assist your organization in enhancing its security posture, there will be some scenarios in which not all recommendations are applicable to your environment. It is common to have customers asking to fine-tune those recommendations; they ask because there are items they consider to be false positives.
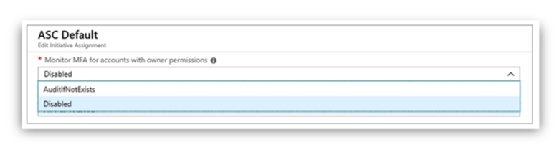
Organizations commonly use a third-party MFA solution for subscription accounts with owner permissions, and the organizations believe they can safely ignore the Enable MFA For Accounts With Owner Permissions On Your Subscription option. However, because the organizations are not addressing this recommendation, there is a 50-point drop in their Secure Score. How can they safely disable this recommendation?
If you are absolutely sure that this recommendation has been addressed by implementing an external factor that is not being taken into consideration by Security Center, you can follow the steps described in Chapter 3, "Policy Management," to disable the policy that reflects your desired recommendation. For the recommendation described in the previous paragraph, you need to choose Disabled from the Monitor MFA for accounts with owner permissions policy drop-down menu, as shown in Figure 4-4.
Using Security Center recommendations to drive a better security posture
Misconfigurations, lack of security expertise, and lack of visibility are the most common reasons for attack vulnerabilities. Azure Security Center recommendations are based on security policies by which you choose to have your environment assessed. You can choose which security policies by which you want Azure Security Center to assess your environment and tell you where your environment is vulnerable. Security Center assesses your environment 24/7 and provides recommendations with a Secure Score Impact. This allows you to prioritize the work that your organization needs to do in order to reduce attack surface and harden your security posture.
ASC continuously assesses your environment -- in Azure or in a hybrid configuration including on-premises or other clouds -- based on the security policies you chose to enable. In addition to providing security recommendations, ASC also maps assessments to several regulatory compliance standards. For each assessment under regulatory compliance, ASC shows how many resources are not passing compliance, and it provides remediation steps. Because of the nature of regulatory compliance assessments, ASC cannot assess all controls. Controls not assessed by ASC does are shown on the list as unavailable (dimmed).
In order to be able to manage and prioritize ASC recommendations and the work required to address those recommendations, ASC provides you with an overall Secure Score per subscription as well as the Score Impact for each recommendation. Score Impact is based on the severity and best practices, and it allows you to identify the top recommendations you should address in order to tighten your security posture and protect your environment.
Michelle Swafford, Principal Program Manager, Azure Security Center Team
About the authors
Yuri Diogenes has a Master of Science in cybersecurity intelligence and forensics investigation from UTICA College and is a senior program manager for the Microsoft CxE Security team, where he primarily helps customers onboard and deploy Azure Security Center as part of their security operations and incident response. Yuri has been working for Microsoft since 2006 in different positions; he spent five years as a senior support escalation engineer for the CSS Forefront Edge team. From 2011 to 2017, he worked for the content development team where he also helped create the Azure Security Center content experience since its launch in 2016. Yuri has published a total of 21 books, mostly covering information security and Microsoft technologies. Yuri also holds an MBA and many IT and security industry certifications, such as CISSP, E|CND, E|CEH, E|CSA, E|CHFI, CompTIA Security+, CySA+, Cloud Essentials Certified, Mobility+, Network+, CASP, CyberSec First Responder, MCSE and MCTS. You can follow Yuri on Twitter at @yuridiogenes or read his articles at his personal blog: http://aka.ms/yuridio.
Tom Shinder is a cloud security program manager in Azure Security Engineering. He is responsible for Azure security technical content and education, Azure security baselining and public cloud security competitive analysis. He has presented at many of the largest security industry conferences on topics related to both on-premises and public cloud security and architecture. Tom earned a bachelor's degree in neuropsychobiology from the University of California, Berkeley, and an M.D. from the University of Illinois, Chicago. He was a practicing neurologist prior to changing careers in the 1990s. He has written more than 30 books on OS, network and cloud security, including Microsoft Azure Security Infrastructure. Tom can be found hugging his Azure console when he's not busy hiding his keys and secrets in Azure Key Vault.






