cloud workload protection
What is cloud workload protection?
Cloud workload protection is the safeguarding of workloads spread out across multiple cloud environments. Businesses that use public and private clouds can use cloud workload protection platforms to help defend themselves against cyber attacks.
Cyber attacks have the potential to severely compromise enterprise systems. In addition, as an organization's use of cloud computing infrastructure grows, so does the attack surface and number of potential vulnerabilities. If an organization is going to use multiple cloud services, then it is a good idea to also use a cloud workload protection platform.
Cloud workload protection technology often relies on two different methods of protection: microsegmentation and bare-metal hypervisors.
Microsegmentation divides the data center into separate security segments before then establishing security protocols for those segments. Bare-metal hypervisor software creates and runs multiple isolated virtual machines (VMs) on a single piece of hardware. If one of these VMs becomes compromised, the issue will not spread to workloads on other VMs.
What is a cloud workload?
A cloud workload refers to the collection of cloud-based resources and processes an application, service or capability needs to work. Examples of cloud workloads include databases, web servers, VMs and containers.
Why is cloud workload protection important?
The workload encompasses the application, its data and the network resources that facilitate a connection between the application and user. Cloud workload protection is critical because, if any portion of the workload doesn't work properly, then the application itself won't function securely and as intended. And, of course, cybercriminal exploitation of a vulnerability in the cloud could result in a data breach or other serious security incident.
Cloud workload security is a complex matter since workloads pass among various hosts and vendors. Although it is not always easy, however, the protection of cloud workloads helps ensure the security of an organization.
Cloud workload security threats
Cloud workload security threats include the following:
- Distributed denial-of-service attacks.
- Human error, such as misconfiguration of access management systems.
- Insider threats.
- Malware.
- Phishing.
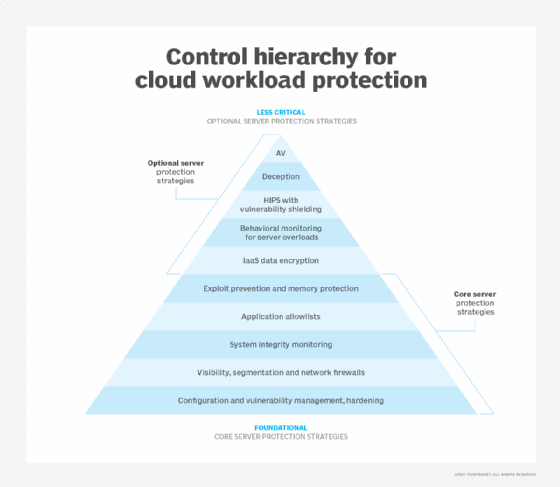
Benefits of cloud workload protection
Cloud workload protection technology can offer the following benefits:
- Consolidation of security logs and alerts within a single dashboard view.
- Better workload visibility and management capabilities across multiple cloud environments.
- Detection of active threats.
- Integration of security into the DevOps continuous integration/continuous delivery pipeline.
- Better vulnerability management.
Challenges of cloud workload protection
Challenges of cloud workload protection arise because workloads may move through multiple cloud-based environments. These environments, in turn, may be owned and safeguarded by multiple vendors. Each of these vendors must play an active role in security and focus on workload protection to eliminate the sort of vulnerabilities that cybercriminals focus on.
Cloud workload security best practices
Cloud workload security best practices include the following:
- Adopting a zero-trust policy.
- Processes to control and keep track of inbound and outbound traffic -- to differentiate between legitimate requests and illegitimate requests.
- Pen testing to gauge the effectiveness of corporate security preparedness.
What is a cloud workload protection platform?
Cloud workload protection platforms (CWPPs) are used to safeguard containers, physical servers, VMs and cloud infrastructures from online threats. They are security tools that home in on the specialized protection needs of workloads across corporate environments.
If an organization uses the cloud, then some experts recommend using a CWPP to manage the associated risks. These platforms help an IT cybersecurity team to assess risk, find vulnerabilities and discover misconfigurations on an ongoing basis -- to ward off online threats.
Differences between CWP and CSPM
The main difference between cloud workload protection (CWP) platforms and cloud security posture management (CSPM) platforms is that CWP concerns itself with cloud-based workloads, while CSPM focuses on cloud-based infrastructure. That said, both focus on safeguarding sensitive information in the cloud.
Popular cloud workload protection vendors and platforms
Cloud workload protection vendors and their respective platforms include the following:
- CloudGuard, with CloudGuard for Cloud Network Security.
- Google, with Google Cloud Platform Security Overview.
- Illumio, with Illumio Core.
- Microsoft, with Microsoft Defender for Cloud.
- Palo Alto Networks, with Prisma Cloud.
- Qualys, with Qualys Cloud Platform.
- Trend Micro, with Trend Cloud One.
- Broadcom, with Symantec Cloud Workload Protection.
- VMware, with VMware Carbon Black Workload.








