
nobeastsofierce - Fotolia
How to use the NIST framework for cloud security
Aligning the NIST Cybersecurity Framework with cloud services such as AWS, Azure and Google Cloud can improve cloud security. Read how to best use the framework for the cloud.
Most security practitioners should be familiar with the NIST Cybersecurity Framework. For practitioners, it provides a lingua franca for security, normalizing discussions for all situations. Any organization can employ the CSF to ensure a strong security posture. It makes the management of security more streamlined and easier and enables better information sharing.
When released in 2014, one initial criticism of the framework was that it wasn't seen as sufficiently specific about cloud environments. Cloud providers have stepped up with additional documentation aimed at any ambiguities in the NIST framework. Cloud providers also aligned their products to the NIST framework for cloud security to help customers achieve safe cloud environments.
How each cloud provider communicates this varies. Let's look at a few of the specific artifacts created and published by providers in detail and discuss how they can be used to follow the NIST framework for cloud security efforts.
Cloud provider support for NIST CSF
AWS
AWS published the white paper "Aligning to the NIST Cybersecurity Framework in the AWS Cloud." It offers a short, concise breakdown of the features built into AWS, aligned to each of the five CSF domains. The document goes area by area through each of the CSF domains -- Identify, Protect, Detect, Respond and Recover -- and correlates AWS features and functions to each.
For example, within the Detect section, AWS includes its Simple Notification Service, access logs -- for example, from S3 -- database logs, CloudTrail, CloudWatch and other features that support detection. AWS also provides threat intelligence collected from different services and then, using machine learning and AI, analyzes log data. It can also connect to customer SIEM systems.
Other areas of the CSF are likewise addressed within the white paper. It includes independent attestation from Kratos SecureInfo that Amazon has "demonstrated the alignment of its adherence to the NIST CSF" via FedRAMP and ISO controls. In other words, this report provides a roadmap of the AWS feature set through the lens of the CSF.
Microsoft Azure
For the Azure platform, Microsoft published a series of documents, each mapped to one of the NIST CSF domains. For example, the document "Microsoft Azure Enables NIST CSF Compliance: Recover Function" outlines specific guidance related to using the Azure platform to accomplish recovery goals. Presented in a more narrative format compared to the report from AWS, the document likewise outlines features available on the Azure platform that support the intent of the CSF.
Microsoft's documentation also discusses areas of shared responsibility between the customer and the service provider, which includes areas where customers need to take action to accomplish their goals. Microsoft provides blueprints for how to follow NIST and other standards with its products. The company also includes an independent attestation from an accredited third-party assessment organization of Azure's alignment with NIST CSF requirements.
Google Cloud
Google published "NIST Cybersecurity Framework & Google Cloud," which explains how to implement the NIST framework for cloud security with its products. Google aligns each of the five CSF domains with different products and briefly explains what each provides customers. The report breaks down each CSF domain ID and the products available to satisfy compliance. It offers brief, bulletlike explanations of why each product is needed for each domain and provides product URLs. For example, under the Identify domain, the document states Forseti Security "uses the Cloud Asset API to collect and store information about your GCP [Google Cloud Platform] resources."
In a separate document, Google provides third-party attestation from cybersecurity advisor Coalfire that Google "implemented the required NIST SP 800-171 controls" but notes three deviations Google made.
Other cloud providers
IBM Cloud and Oracle Cloud also offer documentation around implementing the NIST framework for cloud security. IBM breaks down what the CSF is and how to develop a risk management program around it. The vendor also describes what products and services it offers to assess an organization's security posture and align the CSF for the cloud.
In its documentation, Oracle explains the NIST CSF and how its cloud products and services align with the CSF's five domains.
Support your program with this documentation
The next logical question for practitioners is how they can employ this documentation to make life easier for them. There are a few ways to do this, but the most obvious way is to use the mapping between the Informative References, which is in the far-right column of the Framework Core.
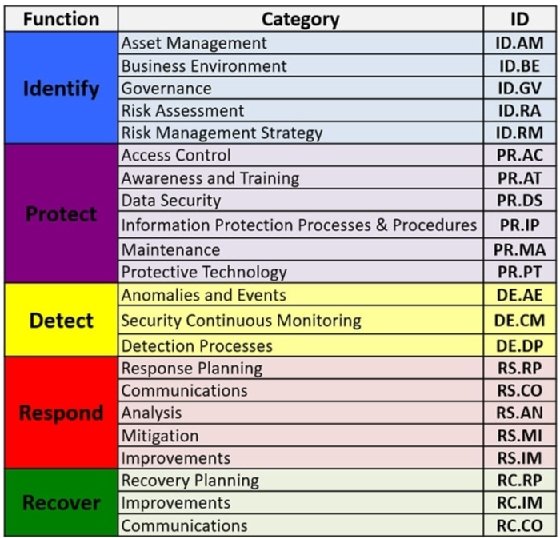
Because each of the categories and subcategories within the NIST CSF is correlated directly to highly visible external references -- such as ISO/IEC 27001:2013, NIST SP 800-53 and COBIT 5 -- a roadmap from the service providers that indexes service features across this spectrum can help directly facilitate compliance activities.
As a consequence of how the CSF is structured, there exists -- for most any regulation -- a mapping or crosswalk between these Informative References and any other regulation an organization might have in scope. Often, these are made available directly from regulators themselves.
For example, the U.S. Department of Health and Human Services -- via the Office for Civil Rights -- published "HIPAA Security Rule Crosswalk to NIST Cybersecurity Framework." If you're a covered entity under HIPAA, you now -- by using these documents in tandem -- have not only a direct mapping to the CSF from HIPAA, and thereby an indirect one to a number of other references, guidance and standards, but also a direct path between services the cloud providers offer and your organization's HIPAA compliance via the documentation from the cloud providers.
This is valuable for compliance activities, but a practically minded security professional might have less use for this than an audit-, assurance- or compliance-focused practitioner. That said, there are also ways security teams can employ this documentation productively. For example, this documentation effectively serves as a function-aligned taxonomy of security features and services offered by a cloud provider.
How is that valuable? In a few different ways. It can be used, for example, as input into risk mitigation discussions. It can also be used to help control selection to address issues that arise as part of threat modeling analyses, and it can be used to help identify compensating controls where other issues are identified.
Alternatively, it can just serve as a reference source for customers to highlight features they have access to and, depending on the documentation in use, responsibilities they might not otherwise know they have.
Further guidance
Beyond the CSF, NIST offers additional cloud security guidance, including the following:






